Governance
Creating Future Value through Transparent Management
Information Protection and Security
Information Protection and Security
SK Networks is acutely aware of the importance of security for personal information/IT services and thus safely protects the company and customers’ information. We have various measures in place to prevent complaints related to corporate data leakage or theft, personal information leakage or theft and information protection, including but not limited to: information security instructions and guidelines; an organization dedicated to information protection tasks; a working-level consultative body joined by CISO(Chief Information Security Officer)/CPO(Chief Privacy Officer); and, employee training on information protection.
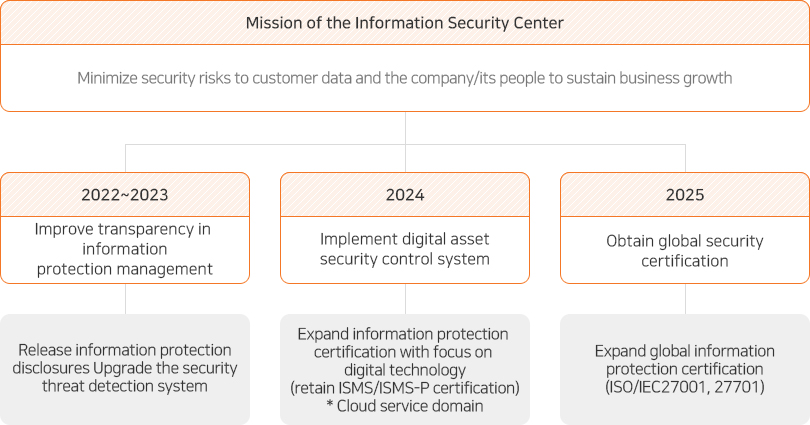
The Information Security Center vows to upgrade the security control system and security certification to minimize security risks in and out of the organization.
Information Security Guideline

SK Networks revised its regulations on personal and company information protection to manage thoroughly and safely protect all personal information handled in accordance with the revision of the three data-related government bills. The revised regulations reflect the disciplinary action to information management that has been strengthened following the liberalization of employees’ PC usage, and Personal information management of all stakeholders, including employees, external company employees, and visitors is handled under this regulation. In addition, we protect valuable information assets by preventing damages, forgeries, alteration, falsification, and leak through the regulations and rules of IT service/security management. The regulations are applied to all divisions, employees, and partners related to information and the system that collects, processes, handles, sends, stores, and manages the information in order to secure safety from various threats.
Certification for Information Security & Personal Information Management System
SK Networks has obtained and maintained ISMS and PIMS certifications, legally obligated since 2015, and plans to newly apply for and acquire ISMS-P11) certification, an integrated certification system, as the existing certifications expire in 2021. We have established information asset identification and risk management plans for this and make it a routine to carry out a series of activities related to vulnerability diagnosis, risk assessment, risk control measures, recurrence prevention, and employee training. The company’s 3-year goal is to acquire ISMS-P certification in 2021 and maintain the certification for 2022 and 2023. We also aim to maintain the level of compliance with the Group Security Guideline, SK group’s standard security guideline, higher than the average among the affiliates.
1) ISMS-P (Personal Information & Information Security Management System)
- Legal grounds: Article 47 of the Act on Promotion of Information and Communications Network Utilization and Information Protection, etc., Article 32.2 of the Personal Information Protection Act, and enforcement decrees, enforcement rules, public announcements of applicable acts.
- Certification agency: Korea Internet & Security Agency (KISA) / an agency designated by the Ministry of Science and ICT
- Certification criteria: Assessment on sustained management system operation for 102 certification items
- The above certification is mandatory for companies in the Information & Communication Services sector with the previous year’s sales over KRW 10 billion or more than 1 million daily users on average during the recent 3months.

Information Security Management Organization
CISO/CPO Business Council
- Information Security
Committeea major executive
decision-making body
: CISO* and others - CISO/CPO Information Security CenterCISO Working Group
Chairman : CISO
- Information Security Director
- Information Security Officer
- 10 Security Divisions Business Division/
Subsidiaries
CISO/CPO Working Group
*CISO: Chief Information Security Officer
SK Networks has designated a dedicated CISO(Chief Information Security Officer) at the executive level, who is prohibited from concurrently holding positions other than information protection. We also operate an Information Security Center that specializes in information protection. The CISO/CPO* Business Council operates on a quarterly basis to discuss essential information protection policies and share significant issues. We are improving the security level of subsidiaries through regular meetings with the CISOs of major subsidiaries such as SK Magic and SK Rent-a-car and level diagnosis based on the SK Group’s security guidelines.
*CPO: Chief Privacy Officer
Security Breach Response
Security Breach Response Procedure
- Notification of incident*
-
Post incident-related information on the website for more than 7 days
Notify the subject and report to a specialized institution within 24 hours - Conduct post-evaluation of the incident and establish recurrence
prevention measures within 1 month of closure - Conduct mock training and report results
*Reporting Procedure: Incident Perceiver → Senior Team Manager & Personal Information Management Division Officer → Senior Team Manager & Risk Management Division Officer → CPO & Team Manager/Executive of Relevant Division → CEO & Executive in charge of Holding Company
SK Networks abides by the Personal Information Breach Response Guideline and Intrusion Incident Response Rules to respond promptly to security incidents. The incident perceiver must immediately report to the person in charge who will take actions based on the severity of the incident. We then comprehend the cause and effect of the incident to take preventive measures and impose disciplinary action based on the violator’s intention, including how much the company was affected by such behavior.
Prevention of Violations on Data Protection and Privacy
SK Networks recognizes the importance of customer personal information and conducts exhaustive protective actions for safe management. In case personal information is included in any stage of the task process, including those handled by our subsidiaries, we make it clear that our privacy policy applies and ensure that employees enter the objectives and reasons for using personal information for more robust security.
Information Security Education
SK Networks publishes information security-related regulations so that all employees can raise their awareness and conducts information security training for employees every year. In 2020, we linked the information security training to the company education platform mySUNI to conduct online training. We internalized the importance of personal information protection and security system by allowing employees who did not receive training offline to check the training materials online. In addition, we prevent information security risks and promote compliance with obligations related to personal information protection by training Walkerhill employees on the importance of personal information protection, affiliated laws and regulations, and collection, utilization, and provision of personal information.

