
Information Protection and Security
SK Networks is acutely aware of the importance of security for personal information/IT services and thus safely protects the company and customers’ information. We have various measures in place to prevent complaints related to corporate data leakage or theft, personal information leakage or theft and information protection, including but not limited to: information security instructions and guidelines; an organization dedicated to information protection tasks; a working-level consultative body joined by CISO(Chief Information Security Officer)/CPO(Chief Privacy Officer); and, employee training on information protection.
The Information Security Center vows to upgrade the security control system and
security certification to minimize security risks in and out of the organization.
Expanding digital tech security management area
- Digital Tech-centered Information Protection Certification
(Maintaining ISMS/ISMS-P Certification)
* Expanding security of Cloud Service area
Establishing an AI-based security management system
- Strengthening response to AI-based cyber attack
* Dark web monitoring, response to exposure of vulnerable information assets (ASM), etc
Securing global-level certification systems
- Expanding global information protection certifications
(ISO/IEC 27001, 27701)
SK Networks revised its regulations on personal and company information protection to manage thoroughly and safely protect all personal information handled in accordance with the revision of the three data-related government bills. The revised regulations reflect the disciplinary action to information management that has been strengthened following the liberalization of employees’ PC usage, and Personal information management of all stakeholders, including employees, external company employees, and visitors is handled under this regulation. In addition, we protect valuable information assets by preventing damages, forgeries, alteration, falsification, and leak through the regulations and rules of IT service/security management. The regulations are applied to all divisions, employees, and partners related to information and the system that collects, processes, handles, sends, stores, and manages the information in order to secure safety from various threats.

Certification for Information Security & Personal Information Management System


SK Networks initially acquired the information security management system(ISMS) certification and personal information management system(PIMS) certification in 2015, and has maintained the revised ISMS-P* certification since its acquisition it in 2021. ISMS-P inspects the overall level of information security and personal information systems with 101 control items, including 16 items on establishing and operating management systems, 64 items on security requirements, and 21 items on requirements in each step of personal information processing. In addition, since 2022, we have disclosed our information protection outcomes to satisfy request from the external organization with public trust and to engage in transparent management of investments and activities related to information protection.
* ISMS-P (Personal Information & Information Security Management System)
- Legal grounds: Article 47 of the Act on Promotion of Information and Communications Network Utilization and Information Protection, etc., Article 32.2 of the Personal Information Protection Act, and enforcement decrees, enforcement rules, public announcements of applicable acts.
- Certification agency: Korea Internet & Security Agency (KISA) / an agency designated by the Ministry of Science and ICT
- Certification criteria: Assessment on sustained management system operation for 102 certification items
- The above certification is mandatory for companies in the Information & Communication Services sector with the previous year’s sales over KRW 10 billion or more than 1 million daily users on average during the recent 3months.
Beyond acquiring the ISMS-P certification and observing laws, SK Networks follows the security guidelines of SK Group. SK Group annually Inspects the implementation of the security guidelines by group members And subsidiaries, and recommends tasks for improvement. SK Networks establishes a plan for implementing SK Group’s recommendations, reports the plan to the top management, and continuously improves its security level by executing the tasks. We are also introducing cloud security posture management (CSPM) and new security solutions to prevent security incidents while establishing a systematic response system in case of a breach.
Information Security Management System
SK Networks appointed the Head of the Information Protection Division as the Chief Information Security Officer (CISO) and Chief Privacy Officer (CPO) to manage, direct, and supervise the information protection and personal information protection duties of the company. A dedicated organization for information protection (Information Protection Team) prevents the leakage of (personal) information and responds to security compliance issues. SK Networks operates an Information Protection Committee, which is the highest decision-making body that comprises key executives and team leaders. The committee reviews, deliberates, and resolves matters and policies related to information protection and personal information protection, makes decisions on disciplinary actions against internal security accidents and violations, and approves action plans according to internal and external security audit results. The discussion results of the Information Protection Committee are reported to the top management. Additionally, we strengthen our ability to execute information protection duties by forming and operating a working-level council on (personal) information protection
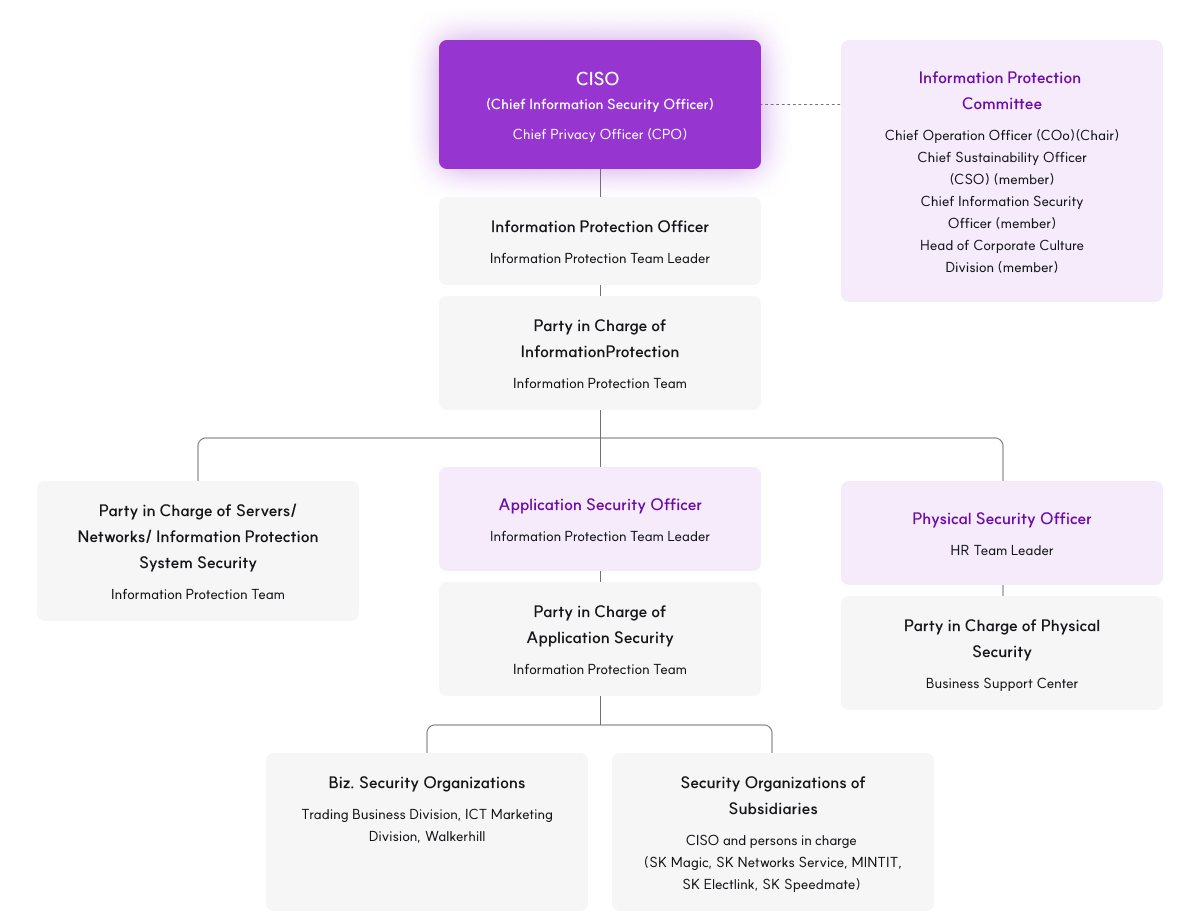
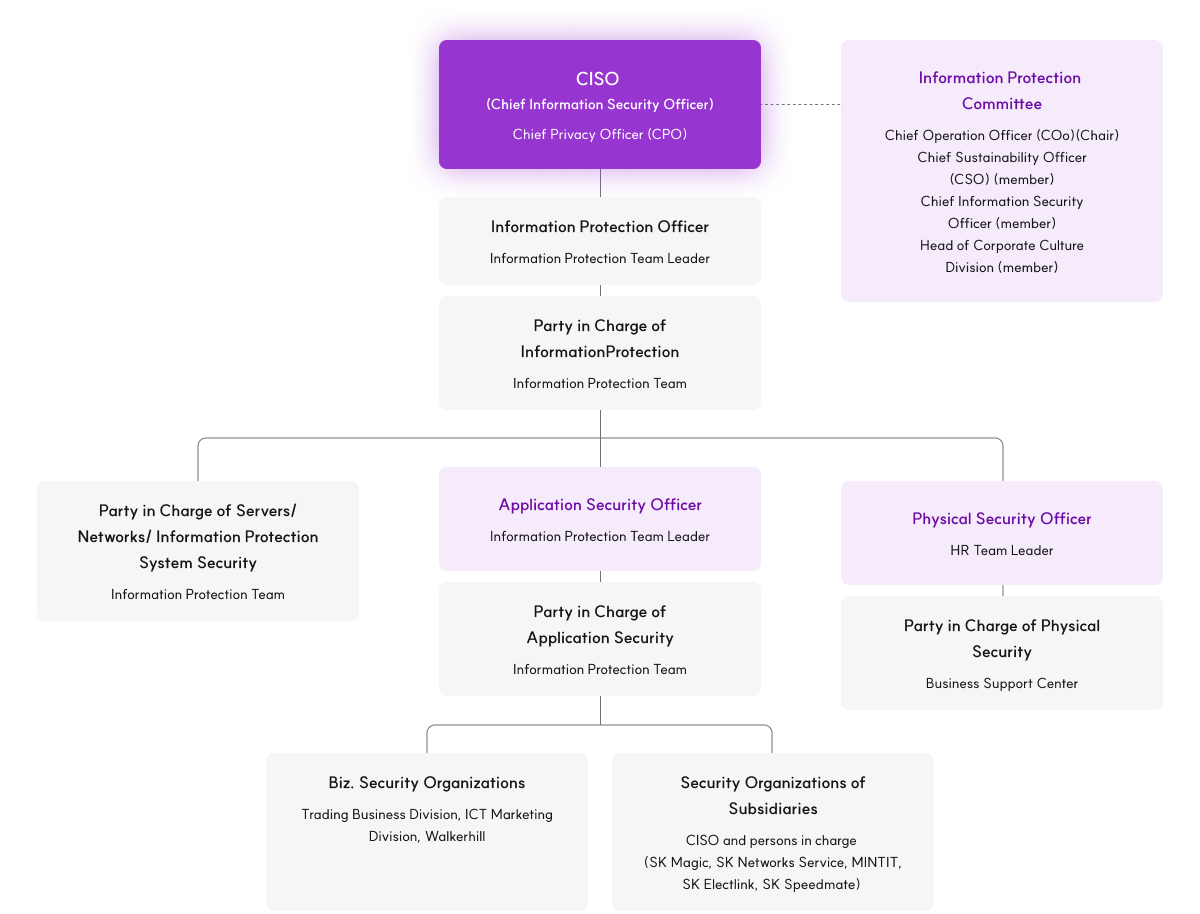
- Information Protection Committee
- Chief Operation Officer (COo)(Chair)
- Chief Sustainability Officer
- (CSO) (member)
- Chief Information Security
- Officer (member)
- Head of Corporate Culture
- Division (member)
- Information Protection Officer Information Protection Team Leader
- Party in Charge of InformationProtection Information Protection Team
- Party in Charge of Servers/Networks/ Information Protection System Security Information Protection Team
- Application Security Officer Information Protection Team Leader
- Party in Charge of Application Security Information Protection Team
- Biz. Security Organizations ICT Marketing Division, Walkerhill
- Security Organizations of Subsidiaries CISO and persons in charge (SK Magic, SK Networks Service, MINTIT, SK Electlink, SK Speedmate, Glowide, En-core)
- Party in Charge of Application Security Information Protection Team
- Physical Security Officer HR Team Leader
- Party in Charge of Physical Security Business Support Center
- Party in Charge of InformationProtection Information Protection Team
Security Breach Response
-
Giving notification* of the occurrence of an accident
-
- Disclosing accident information on the website for seven days or longer
- No tifying the information subject and reporting to the specialized agency within 72 hours
-
Reviewing after supplementation
(committee and BOD) -
- Conducting post evaluation on the accident and establishing preventive measures within one month after the conclusion of the accident
-
Conducting mock training and reporting results
* Reporting procedure : Person who recognizes the accident → Upper-level team leader and person in charge of the company wide personal information division → Upper-level team leader and person in charge of the company-wide risk management division → CPO and team leaders/executives of relevant divisions → CEO and executives of the holding company
Prevention of Violations on Data Protection and Privacy
SK Networks recognizes the importance of customer personal information and conducts exhaustive protective actions for safe management. In case personal information is included in any stage of the task process, including those handled by our subsidiaries, we make it clear that our privacy policy applies and ensure that employees enter the objectives and reasons for using personal information for more robust security.
Enhancing Security Awareness Among Employees
SK Networks announces the enactment and revision of regulations related to information security to ensure that employees can be aware and publishes the regulations so that they are available for review, and it provides updates on major changes in laws and internal policies through regular information security campaigns. All employees sign the information protection pledge each year and are obliged to complete online (personal) information protection education at least once a year. Additionally, we frequently share information about various security accidents and major policy changes and strengthen the security awareness of employees through periodic mock trainings and on-site inspections. In 2023, we built a system for managing the security level of each individual and have continued to improve the security level of individuals and organizations
